Introduction
This will be a post about my very first job in information technology, or IT. For my very first job in IT, I worked as a temporary worker for Data Networks, an IT services company based in the Baltimore area. There wasn't a direct path as to how I got there. It just sort of happened. The story does involve many different locations in and around both Baltimore, MD and Columbia, MD. Here is a map of many of the key locations.
 |
| Key Locations in Baltimore and Columbia, MD |
Student at the UMBC Training Center
During the spring of 2017, I was working at the Target on Dobbin Road in the Columbia Crossing shopping center in Columbia, MD for a mere $10.57 per hour as a part-time employee. I was working as a Team Member in the backroom. Basically, it was my job to make sure that the store's shelves were stocked for the store's customers. Since it was a job that required me to be on my feet for long stretches of time, I developed plantar fasciitis in my left foot. As you can imagine, I wasn't a very happy worker. The final straw with Target occurred when store management tried to blame me for not meeting their goals for online sales during Christmas. I didn't know how to react when they said that. On the other hand, the job at Target did get me away from my roommates for a little bit.
 |
| Map of Target in Columbia, MD |
At the time, I was occasionally going to the Columbia Workforce Center at 7161 Columbia Gateway Dr, looking for a new job. I would and browse through the available job openings on one of the computers that belonged to the Maryland Department of Labor. Feeling frustrated at not finding work for a former Department of Defense contractor that no longer had a Top Secret security clearance, I made an appointment to see a job counselor. After a brief interview, the job counselor, whose name I can no longer remember, informed me that the State of Maryland had a severe shortage of workers in Information Technology. She informed me that the State of Maryland (or was it Howard County?) had an agreement with the University of Maryland-Baltimore County (UMBC) to encourage more workers to go into Information Technology. Basically, the State of Maryland would pay the cost of tuition (around $5,000) to attend the training classes for the A+, Network+, and Security+ certifications given by UMBC at their training center in Columbia at 6996 Columbia Gateway Dr.
 |
| Location of Columbia Workforce Center and UMBC Training Center |
After a short conversation with the person in charge of the UMBC Training Center, I informed the Columbia Workforce Center that I wanted to enroll in the program. The A+ certification class lasted four weeks with classes on Tuesday and Thursday nights. The Network+ class lasted two weeks. The Security+ class lasted an additional two weeks. All of the instructors for the three classes had decades of experience working in information technology. The instructor for the A+ class had a long list of IT certifications in his biography. The instructor for the Network+ class did computer networking for Sandy Spring Bank in Maryland. For the Security+ class, one instructor worked as an independent IT contractor, while the second instructor worked at Booz Allen Hamilton as a cyber security analyst. The students that attended the classes all came from different backgrounds. Some had already worked in IT; meanwhile, others were just getting started.
My First Job in Information Technology
During the A+ class, at the urging of the instructor (whose name I cannot remember), I started to look for entry-level work in IT as a way to get experience. Shortly after updating my resume and posting it on Indeed, I received a phone call from a recruiter (Aaron Webster) at a staffing company based in Hanover, MD called Latitude, Inc. He said that he was looking to fill a job opening a network technician. He said that the job involved working with an IT services company based in Hunt Valley, MD called Data Networks. The recruiter said that Data Networks had a contract to replace old network switches and install new network switches at various high schools in the Columbia, MD area.
 |
| High Schools IVO Columbia, MD |
The recruiter gave the following details about the job:
- The entry level network technician position was temporary.
- The position paid only $10.00 per hour.
- The position involved driving to each job site.
- Data Networks would provide me with a polo shirt to wear during work.
I think that I was also told that the job wouldn't start until July.
Without missing a beat, I agreed to doing the job.
The timing of the job wasn't ideal, however. The lease on my apartment near the Columbia Mall was set to expire on June 30th. One roommate decided to move out of the apartment in the middle of the night a couple of weeks prior to the expiration of lease. That roommate had become somewhat disillusioned at working at NSA as a DoD contractor. My second roommate was trying to figure out what he wanted to do. He was trying to find a new DoD contracting job overseas. For me, I decided to quit my job at Target in order to focus on the job with Data Networks.
My mindset for the temporary job with Data Networks was to do such a good job that they would offer me a permanent job. That was my goal.
 |
| Data Networks of Hunt Valley, MD |
Lastly, at the time, cancerous tumors began to appear on my body at seemingly random places, such as the right side of my neck, my right arm pit, and my right thigh.
Meeting the Team
Shortly after my interview with Latitude, Inc., I received a phone call from Nancy Stout, the Director of Human Resources at Data Networks. We exchanged contact information. She asked me what my shirt size was. (Note to Nancy: I never did receive my blue polo shirt with the Data Networks logo on it.) She also scheduled a time for me to visit the Data Networks office in Essex, MD, so that I could meet the rest of the team members.
 |
| Nancy Stout of Data Networks (Source: LinkedIn) |
After that phone call with Nancy, events moved at a lightning-fast pace. The moving company showed up at my apartment at Columbia Mall and shipped the items that I was keeping back to my mom's house in Arizona. I finished emptying out my remaining items from the apartment. I turned in my apartment key to the rental agency. I then used Hotwire to reserve a room for two weeks at the Ramada Hotel in Hanover, MD near BWI Airport along Maryland State Route 100. Ironically, the Ramada Hotel was a short distance away from the Latitude, Inc. office building where I had an in-person interview for the entry level network technical job.
Driving to the Configuration Center
Shortly after moving out of my apartment, I received a phone call from Nancy Stout. She stated that the Data Networks personnel in charge of the project wanted to meet me prior starting work. She said that they wanted to have a short meeting at the Data Networks Configuration Center in Essex, MD, a small town outside Baltimore on the Pulaski Highway. She gave me the date, time, and address for the interview. She said that I should ask to speak to either Lovett Davis or Todd Rechen, the two project managers.
Shortly after the phone call, I remember going to the Burlington Coat Factory at the Arundel Mills Mall to buy a new dress shirt and tie, a new pair of dress pants, and a pair of dress shoes the day before the interview. Despite the weather being 95 degrees Fahrenheit with 90% humidity, just your typical summer weather in Maryland, I dressed for the interview as if I was going to an actual job interview. I probably could have gotten by wearing a nice pair of shorts and a polo shirt with socks and shoes, but I wasn't going to take that chance. I wanted to make a positive first impression. Like I wrote earlier, I was hoping to get a full-time job with Data Networks.
I then got into my car and drove northwest on Highway 100 and took the exit for Interstate 895, heading northeast to Baltimore. I entered the city limits of the City of Baltimore. I then drove through the Fort McHenry tunnel that goes under the Inner Harbor. Once on the other side of the tunnel, I stayed on Interstate 895 until I took the exit for the Pulaski Highway. From there, I drove up the Pulaski Highway until I made a right turn onto Rossvile Blvd, right next to the Wawa gas station. The Data Networks Configuration Center was a short distance down the street. The entire area was a light industrial area. The Data Networks Configuration Center was located in a non-descript industrial park. It was just one office in a long row of offices. If I remember correctly, there was just a simple sign on the front of the door that read "Data Networks". The entire drive from Hanover, MD to Essex, MD took over an hour.
I seemed to have found the right place. I parked the car and locked the doors. I straightened out my clothes. I took a deep breath and then opened the office door for Data Networks.
I want to write that the very first person I met as I walked in the door was Michael (Mike) Keller. He was one of the senior technicians at Data Networks that would be working on the Howard County Public Schools project. I remember he told me that he had a lot of IT certifications from Dell Technologies and VMware. After a short introduction, he took me into an office where I met both Lovett Davis and Todd Rechen, the two leaders of the project. If I remember correctly, Lovett Davis had IT certifications for CompTIA's A+, Network+, and Security+. He may have given me his business card, which is why I remember those three specific IT certifications. Todd Rechen, on the other hand, had both a bachelor's degree and a master's degree in Computer Science.
 |
| Senior System Engineer Mike Keller of Data Networks (Source: LinkedIn) |
The meeting itself was a breeze. Lovett, Todd, and Mike just wanted to meet me prior to getting started on the project. They also just wanted to know what kind of IT experience, if any, that I had. I explained that I was an unemployed former DoD contractor without a Top Secret clearance that was looking to go into IT. I also explained that I was taking the classes for A+, Network+, and Security+ at the UMBC Training Center in Columbia, MD. I might have mentioned that I quit my dead-end job at Target to work on the project. At the time, I had a rather large cancerous tumor right below the right side of my jaw. I'm not too sure what they thought about that. Anyway, it was a very friendly interview.
 |
| Director of Enterprise Services Lovett Davis of Data Networks (Source: LinkedIn) |
After the short interview, Lovett and Mike gave me a short tour of the Data Networks Configuration Center. They gave me a brief rundown about the HP Aruba switches that were going to be used on the project. I remember seeing worktables with several stacks of brand new Hewlett Packard Enterprise (HPE) Aruba multilayer switches that had been taken right out of the box. Lovett explained that Howard County Public Schools had several high schools that were using old switches (Sorry, I don't remember the name of the brand.) in their campus LANs that needed to be replaced.
HPE Aruba Multilayer Switches
 |
| HPE Aruba 2930F Switch (Source: HPE) |
Here is just a quick note about the HPE Aruba multilayer switches. Going through HPE's website, it is very conceivable that we were going to install a variant of the HPE Aruba 2930F switch. The photo of the HPE Aruba 2930F switch looks very similar to the switch I remember installing numerous times while working on the project. The array of ports along the face of the switch and the distinctive Aruba with rounded letters in orange looks very familiar. I remember writing down the product name IOT look it up on HPE's website when I got back to my hotel at the end of the day. Anyway, I do remember reading on HPE's website that the specific switch we were going to install was a multilayer switch. That is, the switch operated at both the Network layer (Layer 3) and the Transport layer (Layer 4) of the OSI Reference Model. Switches typically operate at the Data Link layer of the OSI Reference Model. At the time, I think HPE had just acquired Aruba Networks. Not that it matters.
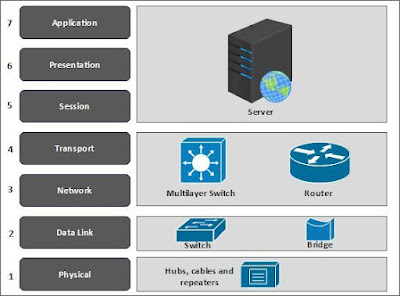 |
| Multilayer Switches operate at Layers 3 and 4 of the OSI Reference Model |
First Day on the Job
Shortly before leaving the Data Networks Configuration Center, Lovett or Todd informed me about the first high school that we were going to work at for the project. Ironically, the high school was very close to the Target on Dobbin Road in Columbia, MD. In fact, the very same Target that I used to work at. The name of the school was Long Reach High School.
 |
| Location of Long Reach High School |
I really didn't know anything about the school apart from driving past it on numerous occasions. However, I was actually going to go there for work. Lovett and Todd told me to show up at Long Reach High School on a Tuesday in July 2017 at around 8:30 AM. I drove over from my room at the Ramada Inn dressed in a blue polo shirt, tan khaki pants, and running shoes. I really didn't know what to expect when I showed up. I was the first person from Data Networks to show up. Not knowing what to do, I got out of my car and stood near the main entrance of the school. Since it was Maryland in July, the weather was already starting to get hot and humid. After standing around for a couple of minutes, Mike Keller showed up. Then Lovett and Todd then also appeared. Then two additional temporary workers showed up (Sorry, I don't remember their names.). The two additional temporary workers were like me. They were hired as temporary workers to assist with the project and, more importantly, get IT experience. Both of the temporary workers were of college age. Lastly, another member of the team showed up. His name was Linwood Brown. He was one of the senior networking technicians for Howard County Public Schools. You could think of him as the customer.
After a brief introduction, Linwood escorted the team into the main building of the high school. After signing in at the administrative office and getting visitor badges, there was a meeting. Lovett went over what the plan for the day was going to be.
Here was the plan for the day:
- Identify all of the locations inside the school where the new switches were to be installed.
- Unload the new switches from the van that Mike drove to the school from the Configuration Center.
- Take the new switches to their assigned location.
- Dispose all of the packaging for the new switches.
Since we started work at 8:30 AM, it didn't take long to finish all of our tasks for the day. I'd say that we were done at about 12:30 PM or so. Right around lunch time. Plus, it helped that school was out for the summer. The only people at the school were the administrative staff. We could get our work done with minimal delays. Before leaving for the day, all of the temporary workers were told to show up at Long Reach High School on the following Thursday at 6:30 AM. Getting off work at lunch time was something of a surprise to me. I was expecting to work a full eight hours. Not only that, I was also expecting to work Monday through Friday. It was then that I realized that not only was the entry level network technician position temporary, but it was also part-time. After my initial disappointment faded away, I got something to eat for lunch and drove back to the Ramada Inn. Once I was back at my hotel room, I started studying one of my A+ or Network+ certification books. Later on that afternoon, I had my Network+ class at the UMBC Training Center in Columbia, MD for three hours.
Project Management and Networking Diagrams
At the time, I didn't realize that there was an actual schedule to replace the old network switches at Howard County Public Schools that Data Networks was following. I remember Todd telling me one day that the entire project had been planned out in detail. There were numerous constraints and requirements for the project. While in the Army in South Korea, I took an introductory class in project management, so I was familiar with some of the steps on how to plan and implement a project. Some of those constraints that needed to be considered for the project were the following:
- The schools in Howard County that required new network switches were all high schools.
- None of the high schools had the same layout or floorplan.
- The project had to be completed during the summer vacation to prevent any service disruptions for students and staff.
- There were only two days available each week to install new switches for each school.
- The first day was required for set-up.
- The second day was required for installing the new switches and for performing any troubleshooting/testing.
- The project had to be within the allotted budget. That would explain why the position was part-time and temporary.
- All old network switches had to be replaced with new HPE Aruba switches.
It's by no means an exhaustive list of requirements, but I am sure that you get the idea.
I don't remember if it was Todd or Lovett, but someone did explain to me that they went through and estimated how many man-hours it would take to complete the various steps of the project. My guess was also that Data Networks would have lost money if there were any delays in completing the project. Thus, the project didn't have a large margin for error.
Networking diagrams are important itmes to have when planning an IT project. The two major networking diagrams are the physical and logical network diagrams. The physical and logical network diagrams are like roadmaps for the network.
The physical network diagram identifies the physical location and function of each network device. It's kind of like a floorplan. The physical network diagram also portrays all of the physical arrangements of the network, such as ports to be used, cable types to be used, the shelf location of devices on each specific server rack, and so on. Depending on the scale of the network, you can have a bird's eye view physical network diagram with additional physical network diagrams for each server closet, for example. Basically, you want to portray where everything goes and what devices connect to each other and how. Here is an example of a physical network diagram.
 |
| Physical Network Diagram Example (Source: Cisco Networking Academy) |
In contrast, the logical network diagram displays the connecting interfaces and the Layer 3 network addressing scheme to be used by the network. Additionally, the logical network diagram shows how the devices communicate with each other and how data flows through the network. A key piece of information on the logical network diagram is the IPv4/IPv6 address to be used by each subnet. You might also want to indicate which specific ports will be used on switches and routers. Here is an example of a logical network diagram.
 |
| Logical Network Diagram Example (Source: Cisco Networking Academy) |
I don't ever remember seeing either kind of network diagram while working with Data Networks. However, I do remember seeing Lovett, Todd, or Linwood consulting a diagram of some sort, especially when they were troubleshooting an issue. I do remember specifically Todd consulting a diagram of some sort to make sure that the switches I installed on a server rack were in the correct server location and in the proper order. In fact, now that I think about it, Todd, Lovett, and Mike did annotate a diagram as we took each HPE Aruba switch to its assigned location at each school.
As Lovett and Todd explained to me, it was important that each HPE Aruba switch get placed in the correct server closet and installed in the correct order on the server rack. It was also important to know the location of each specific switch for simple accountability purposes in addition to the performance of the network.
All of that planning had been accomplished at the Data Networks Configuration Center in Essex, MD before I worked on the project.
In other words, you just couldn't install a new switch just anywhere.
Second Day on the Job
Based on a recommendation from Mike Keller, I went to Home Depot in Columbia, MD, just a short drive down Snowden River Parkway, to buy two screwdrivers. I bought a flathead screwdriver and a cross-tip screwdriver. Both screwdrivers had to be seven or eight inches long. Those two screwdrivers would prove themselves to be rather helpful.
On Thursday morning, I got up at 5:00 AM. I left my hotel room at the Ramada Inn by 5:30 AM. It was too early for the complementary hotel breakfast, so I drove to a nearby McDonald's for a quick breakfast. I think I arrived at the Long Reach High School parking lot at about, say, 6:20 AM. Mike and Todd had just arrived. Lovett was on his way. The other two temporary employees arrived a couple of minutes after me. At around 6:30 AM, Linwood Brown arrived. He unlocked the main door to the school and let everyone inside.
 |
| Ethernet Cable |
After a short planning meeting, it was decided that I would work with Mike on this day. We walked down a hallway and found our first server closet. From what I remember, it was more like a small room than a closet. Linwood unlocked the door. Inside the room was a server rack consisting of five switches that were still powered on. I noticed that the power cables and the Ethernet cables were daisy-chained to each switch. To the side of the server rack was a stack of five brand new HPE Aruba switches (with cables) that had been put inside the room on Tuesday. With Mike's assistance, I performed the following steps:
- Turned off all of the old switches.
- Disconnected all of the power cables from the old switches.
- Disconnected all of the Ethernet cables from the top old switch.
- Disconnected all of the fiber-optic cables from the old switches.
- Unscrewed all of the screws that connected the top old switch to the server rack.
- Removed the old switch from the server rack.
- Placed the old switch and power cables outside the server closet.
I then went to the stack of new HPE Aruba switches. Each new switch was labeled with a number on the bottom. For server racks, the switch with the lowest number (number one) went on top of the stack. Then the switch labeled with a number two was placed under the switch labeled with the number one and so on until you were out of switches to install. I flipped over each new switch, looking for the switch with a number one. Once I found the switch with a number one label, I then mounted the switch to the top rack of the server rack. I then re-connected the Ethernet cables to the ports on the new switch from the switch below. I then moved on to the second old switch from the top, disconnecting all of the Ethernet cables. I then removed the old switch from the server rack. I then located the new HPE Aruba switch that was labeled with number two. I then mounted the new switch to the second rack from the top of the server rack. I then re-connected all of the Ethernet cables to the switch. I performed the same steps for the rest of the old switches on the rack that needed to be replaced, ensuring that the new switches were being mounted in the correct order. It was a slow, deliberate process to replace all of the old switches. Mike then assisted me with re-connecting all of the Ethernet and fiber-optic cables with SC connectors to the new switches. A key point here is that sometimes the server closets were in horrible condition with Ethernet and fiber-optic cables strewn all over like a bowl of spaghetti. Cable maintenance is paramount. You want the cables to be neatly organized. You probably should also label any important cables for any future problems. I then daisy-chained all of the power cables to the switches before turning on all of them on.
 |
| Fiber-Optic Cable with SC Connectors |
Once all of that was completed, Mike then opened his laptop and then connected a sky-blue console cable from the laptop to one of the switches. He then used a program called PuTTY, a terminal emulator, to configure the switches. Basically, he was providing configuration information for each port to the switch and then saving the configuration. We then cleaned up the area and made sure to neatly stack all of the old switches and their power cables before moving on to the next server closet.
 |
| PuTTY Configuration Screen |
Those were the basic steps that all of the members of the team performed at each location inside the school that required a new switch. Most of the time, the old switches were stacked inside a server closet. Other times, the old switch(es) would be located on top of a storage cabinet or some other location that was difficult to find. Just a note that working inside server closets gets really H-O-T!!! After working in my first server closet, I was covered in sweat. It probably didn't help that oftentimes the air conditioning inside the high schools was turned off except for the administrative offices. As the morning wore on, the plantar fasciitis started to get painful, so I started to drag my left foot everywhere I walked.
After working with Mike on a couple of server closets, I started to work on server closets on my own. The whole process of removing old switches and then mounting the new switches became rather easy. This allowed Mike to check the work of the other two workers. Todd would help out with server closets as well. Once all of the new switches had been mounted, turned on, and configured, Lovett and Linwood would then do all of the testing on the new switches. More often than not, each high school had a room that resembled a Network Operations Center (NOC) from where the computer network could be centrally managed.
What were Lovett and Linwood doing? Well, I imagine that they were sending a series of what are known as ping commands to each switch. The ping command will let you know if a device (host, switch, router, other) is connected to the network. If you don't receive a successful response to a ping request, then the device you are attempting to ping might not be on the network. Typically, there are several items that you might want to ping after setting up a network. The items that you may want to issue a ping command to include the following:
- Pinging the IPv4/IPv6 address of the device itself to ensure that the TCP/IP stack is functioning properly.
- Pinging another device on the same network.
- Pinging the IPv4/IPv6 address of the default gateway on the assigned router to ensure that the device is able to send messages to another network.
- Pinging the IPv4/IPv6 address of a device on another network.
If a one of the issued ping commands fails, then you might have a problem that needs further investigation.
 |
| Ping Command Example |
Another command that you can issue is known as the tracert, or traceroute, command. This command is similar to the ping command. However, there is a difference. The tracert command will attempt to follow the path of the message. The tracert command will display the information of each router it encounters on the way to the destination device. If the tracert command fails along the route, the tracert will provide you with the information of the last known router it successfully detected. With that information, you might have a clue on where to look for a connectivity problem.
 |
| Tracert Command Example |
Thus, if the Lovett and Linwood were probably pinging each new switch from the NOC. If the ping command was unsuccessful, then they would issue the tracert command to determine where the problem may lie. Once they were able to identify where to look for the connectivity problem, it was a matter of going to the appropriate server closet and trying to resolve the connectivity problem. Sometimes it was a matter of either the Ethernet cables or the fiber-optic cables being connected to the wrong port on the switch. Other times, there were problems with the cabling of the network itself. All we could do was wait for Lovett, Linwood, and Todd to diagnose the problem and then try to resolve it. Troubleshooting network problems can be really tedious to experience firsthand. Personally, I made every attempt to see what it was they were doing in order to learn more about networking.
Once the testing and any troubleshooting were complete, it was time to clean up. That meant to go around to each server closet and pick up all of the used switches and their power cables. The used switches and power cables were usually then taken back to the walkway near the main entrance. At that location, we inventoried all of used switches to ensure that we had all of them. After the inventory, we typically stacked all of the used switches on a pallet for someone from Howard County Public Schools to pick up.
 |
| The End Result (Photo by Me) |
Once the inventory was complete, we were finished for the day. That second day at Long Reach High School seemed to take forever. We probably worked close to seven hours that day. I didn't care a whole lot as the work was interesting. As a bonus, I enjoyed working with my co-workers. It was a breath of fresh air after working in the trenches of consumerism at Home Depot and Target. With each succeeding high school we worked at, the days went by faster. I got to the point where I could disassemble the old network switches and then mount the new network switches on my own without any help. After I completed work at the server closet, Mike would perform a quick check of my work and then tell me where I needed to go next.
The Final Total
So how many high schools in Howard County, Maryland did I work at with Data Networks? That is a really good question. I can't give an accurate answer as all of the notes that I took during that period of time have been thrown away. Let's see if I can reconstruct the schools that I worked at with a table in HTML. Before I do that, let me take another look at that map of high schools that I created in Google Maps to jog my memory.
Thus, if my memory is correct, it looks like I replaced the network switches for a total of five high schools for Howard County Public Schools. I thought that the total number of schools would be higher, but it looks like I was wrong. I do remember one school we worked at was actually two schools (a middle school and a high school) at one location. Before I left the project, the next high school on the list would have been Howard High School.
Leaving the Project
While working with Data Networks on the project with Howard County Public Schools, I was talking to a classmate at the UMBC Training Center about getting a new IT job. One Tuesday or Thursday night before the A+, Network+, or Security+ class (I don't remember which), a classmate, Jason Partington, told everyone that he worked as an IT help desk agent at the Social Security Administration (SSA) in Woodlawn, MD. He said that his company, Koniag Government Services (KGS), was always looking to hire new IT help desk agents due to a high employee turnover rate for the position. He also added that KGS would hire people for the position if they didn't have any IT certifications. Jason said that before he started working at SSA, he was a cook at Ruth Chris steak restaurant in Pikesville, MD. Thinking that working at SSA as an IT help desk agent would be a good entry-level gateway into IT, I gave Jason my phone number and my email address. He said that he would let KGS Human Resources know that I was interested in the position. Later that night at my hotel room in a Red Roof Inn, I went to the KGS website and applied for the position. I also made sure to mention Jason's name during the application process. Sure enough, a few days after applying for the IT help desk agent position, I received a phone call from KGS Human Resources. The person I spoke to said that KGS had received my application and that Jason had referred me for the position. After a couple of questions, I was told that I would receive a phone call from the senior agent on the SSA contract in the next couple of days. She said that it would be an informal interview to gauge what I know about IT and to not get too stressed during the phone call. A couple of days later, I received a phone call from the senior agent. We spoke on the phone for about 20 minutes or so as I answered basic questions about IT and the importance of customer service. Considering that the phone call was at 9:00 AM, I thought that the phone call went well. After several more days went by, I received another phone call from KGS HR to schedule an interview with the project managers for the IT help desk agent contract at KGS' office in Woodlawn, MD on Lord Baltimore Road. At the interview, one of the project managers I met was Bryan Cronin. We talked about my work history, what I knew about customer service, what I knew about IT, and what the expections were for being an IT help desk agent on the contract. It also helped that Bryan, like me, was in the military. He had been in the U.S. Air Force. The interview was positive and lasted about an hour. After waiting several more days, I received yet another phone call from KGS HR. I was offered the IT help desk agent position at SSA as a KGS employee. I accepted the job offer.
After finishing work at another high school, it might have been either Hammond High School or River Hill High School, I informed Lovett, Todd, and Mike that I had accepted a job offer to work as an IT help desk agent at SSA. Everyone was happy with my announcement. It was more than a little bittersweet to leave the project with Data Networks. I really enjoyed working on the project. I learned A LOT. More importantly, I enjoyed working with my co-workers. It as difficult to leave the project, but the IT help desk agent position was a new opportunity in IT. I ended up working as an IT help desk agent at SSA for six years.